Goal of the Document is to demonstrate the step-by-step procedure to create the CA using OpenSSL on Windows and getting the Certificates signed from the CA created.
NOTE:- This can only be used for testing puposes and cannot be used for Production Systems and this would be Private CA and will not be providing Security as provided by Authorised CA bodies.
Step1. Download and setup the open SSL Environment
Download the required binaries from the below link:
http://www.openssl.org/related/binaries.html which refers you to
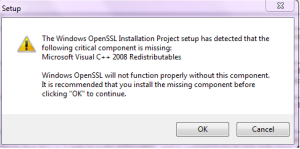
This link will also offers you to download “Visual C++ 2008 Redistributable for Windows” without which you will not be able to run openssl binaries and will hit the below Error. So download the openssl appropriate for your machine along with the Visual C++ Redistributable :-
Once Installation is completed you will get the folder name “C:\OpenSSL-Win64” created under C:/ by default. (Name may vary according to the binaries used)
In order to identify the windows to openssl commands set the C:\OpenSSL-Win64\bin in your computer system PATH variable
Open a DOS Command Prompt
Navigate to the OpenSSL Binaries directory type
cd C:\OpenSSL-Win64\binCreate the private key. Type
openssl genrsa -des3 -out PrivateRootCA.key 4096This will create a Private Key named “RootCA.key”
When prompted enter a *very* strong password
And then verify the password
Create the public key. Type
openssl req -new -x509 -days 365 -key PrivateRootCA.key -out PrivateRootCA.cerWhen prompted enter the *very* strong password
For Country Name enter the international standard two letter abbreviation (use GB, NOT UK if in the UK)
For State enter the state name in full, or for IN the county name
For Locality, enter where your company is registered, town or city
For organization name enter either the full company name e.g. Mycompany LTD
For organization unit enter Development or Support
For common name use your domain name e.g mycompany.com
For email address enter a valid address e.g. support@mycompany.com Or you can leave this blank and hit Enter
This will create a Public Key for the root ca named “PrivateRootCA.cer”
Now you are done with creation of a Root CA who can sign your Certificates.
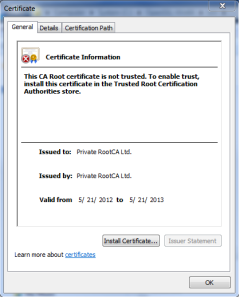
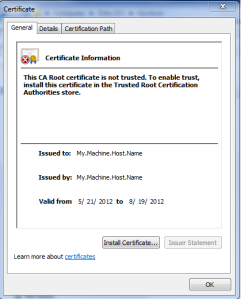
You can verify the Root CA by double clicking on RootCA.cer and you would see Issuer and Owner to be same as below:-
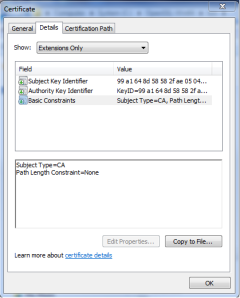
From above screen shots you it can be verified as the Subject Type is CA.
In order to use this certificate as trusted certificate for your windows machine please install the certificate in to your Windows trusted CA list as below:-
1. Double Click on the certificate named RootCA.cer
2. Click on “Install Certificate” button at the bottom in the General Tab
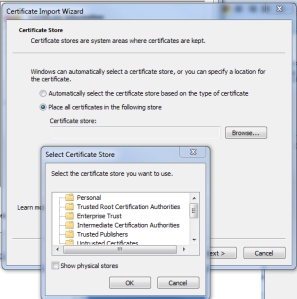
3.You will get below screen and click on “Next”
4.Clicking on the next you will get below screen in this select “Place all certificate in the following store” and in the popup window select “Trusted Root certification Authorities” and click “Ok” and Finsh
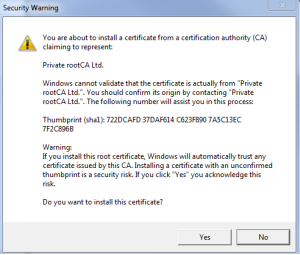
5.Once you finish importing the new Trusted Root CA into the store you will get below warning appearing into the windows
Please read through the same and say yes if you are fine with this.If not please do not import the Rot CA into your Windows trust Store.
Generate a self signed certificate using
keytool -genkey -alias server_cert -keyalg RSA -keypass privatepassword -keystore keystore.jks -storepass password ( create a key pair )
keytool -export -alias server_cert -file self-signed.cer -keystore keystore.jks ( export the certificate from keystore keystore into a file, say self-signed.cer
keytool -certreq -v -alias server_cert -file server.csr -keypass privatepassword -storepass password -keystore keystore.jks
Once above 3 commands executed you will get three files named
keystore.jks
self-signed.cer
server.csr
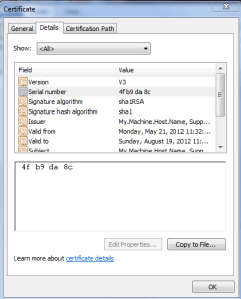
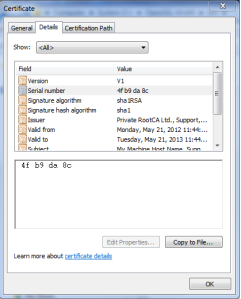
Now double click on the file named “self-signed.cer” and click on “Details” Tab inside details tab click on the “Serial number” on the lower box you will find a hex values something like
and keep it saved somewhere we would need it in the next step.
Now copy the file named “server.csr” to location “C:\OpenSSL-Win64\bin”
Execute the below command:-
openssl x509 -req -days 365 -in server.csr -CA PrivateRootCA.cer -CAkey PrivateRootCA.key -set_serial 0x4fb9da8c -out server.cerOnce above command is executed successfully you will get a file named “server.cer” created on the same location.
Double Click on the file named “server.cer” and you will see as below:-
Where the things to be noticed are “Issued to” and Issued by” which are showing it as the signed by Private RootCA Ltd.
Now go to “Details” tab and check whether the signed certificate has been generated with the same Serial as self-signed certificate:-
Check in the Certification Path and you would be able to see hierarchy of the certification:-
Now copy the server.cer and PrivateRootCA.cer file to the location where you have created/generated your keystore.
Execute below command to import the RootCA.cer certificate into your keystore as this is needed to be present in the keystore before importing the signed certificate.
keytool -import -v -noprompt -trustcacerts -alias rootcacert -file PrivateRootCA.cer -keystore keystore.jks -storepass passwordOutput Would be as below:-
Certificate was added to keystore
[Storing keystore.jks]
Now import the Signed certificate into your keystore
keytool -import -v -alias server_cert -file server.cer -keystore keystore.jks -keypass privatepassword -storepass passwordOutput would be as below:-
Certificate reply was installed in keystore
[Storing keystore.jks]
Which implies the Signed certificate had been imported successfully.
Now list the keystore and verify that the certificate chain had been created successfully in the keystore:-
keytool -list -v -keystore keystore.jks -alias server_cert -storepass passwordYou would see the output as below:-
D:\keystore>keytool -list -keystore keystore.jks -v -alias server_cert
Enter keystore password:
Alias name: server_cert
Creation date: May 21, 2012
Entry type: PrivateKeyEntry
Certificate chain length: 2
Certificate[1]:
Owner: CN=My.Machine.Host.Name, OU=Support, O=Oracle, L=KA, ST=Ban, C=IN
Issuer: CN=Private RootCA Ltd., OU=Support, O=Oracle, L=BAN, ST=KA, C=IN
Serial number: 4fb9da8c
Valid from: Mon May 21 11:44:04 IST 2012 until: Tue May 21 11:44:04 IST 2013
Certificate fingerprints:
MD5: 5F:FF:6F:8A:C5:22:3D:51:23:A8:FF:AF:96:5A:98:BB
SHA1: 29:4A:14:5A:42:31:57:94:57:3A:CA:B4:E2:AB:00:90:D5:69:96:1C
Signature algorithm name: SHA1withRSA
Version: 1
Certificate[2]:
Owner: CN=Private RootCA Ltd., OU=Support, O=Oracle, L=BAN, ST=KA, C=IN
Issuer: CN=Private RootCA Ltd., OU=Support, O=Oracle, L=BAN, ST=KA, C=IN
Serial number: 9126d09b3c5e8c3c
Valid from: Mon May 21 11:40:41 IST 2012 until: Tue May 21 11:40:41 IST 2013
Certificate fingerprints:
MD5: 7A:8E:2A:3B:19:51:8C:F7:B3:3A:31:CE:78:30:DF:E6
SHA1: B7:7D:58:B2:85:EC:44:15:FB:78:F6:B3:4E:A3:AD:A4:25:5C:B4:C2
Signature algorithm name: SHA1withRSA
Version: 3#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 99 A1 64 8D 58 58 2F AE 05 04 4B 3D C4 35 EA 39 ..d.XX/…K=.5.9
0010: 04 E3 8F 7F ….
]
]
#2: ObjectId: 2.5.29.19 Criticality=false
BasicConstraints:[
CA:true
PathLen:2147483647
]
#3: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 99 A1 64 8D 58 58 2F AE 05 04 4B 3D C4 35 EA 39 ..d.XX/…K=.5.9
0010: 04 E3 8F 7F ….
]
]
D:\keystore>
Where you can see the Certificate[1] as your server certificate and Certificate[2] as RootCA certificate who signed the certificate.
From the Admin console, go to your server page, and in the Keystore&SSL tab choose:
Custom Identity and Custom Trust
Custom Identity
Custom Identity Key Store File Name: keystore.jks
Custom Identity Key Store Type: jks
Custom Identity Key Store Pass Phrase: password
Confirm Custom Identity Key Store Pass Phrase: password
Custom Trust
Custom Trust Key Store File Name: keystore.jks
Custom Trust Key Store Type: jks
Custom Trust Key Store Pass Phrase: password
Confirm Custom Trust Key Store Pass Phrase: password
Private Key Alias: server_cert
Passphrase: password privatepassword
Confirm Passphrase: privatepassword
Ensure that SSL Listen Port Enabled is selected, then restart your server.
You are done.
WebLogic is now configured successfully to do one-way SSL (no client authentication).



Reblogged this on lava kafle kathmandu nepal.
Comment by lkafle — August 9, 2012 @ 9:37 am
We followed the steps above. The only problem we face is taht when I want to change something in de weblogic console we getting errors. In the log file I seer errors like
BAD_CERTIFICATE alert was received from ….Check the peer to determine why it rejected the certificate chain (trusted CA configuration, hostname verification). SSL debug tracing may be required to determine the exact reason the certificate was rejected.
Comment by Remko — January 25, 2013 @ 9:44 pm
Everything is very open with a precise clarification of the issues.
It was really informative. Your site is extremely helpful.
Many thanks for sharing!
Comment by table and chairs for kids — February 9, 2014 @ 4:31 am
Hey very nice website!! Man .. Beautiful .. Amazing .. I will bookmark your site and take the feeds also…I’m happy to find so many useful info here in the post, we need work out more techniques in this regard, thanks for sharing. . . . . .
Comment by borvestinkral — July 17, 2017 @ 4:34 pm